Japan’s Data Privacy & Cybersecurity Rules (2025): APPI, Breach Reporting, and Cross-Border Transfers Explained
TL;DR
Japan’s APPI now reaches foreign firms, mandates strict breach reporting, and limits overseas transfers unless safeguards match Japanese standards. Pair that with growing ransomware threats, METI cybersecurity guidelines, and sector-specific rules, and US companies must localise privacy policies, vet vendors, and harden defences to stay compliant and resilient.
Table of Contents
- The Act on the Protection of Personal Information (APPI): Core Principles
- Core Obligations for Businesses Under the APPI
- Cross-Border Data Transfers
- The Cybersecurity Landscape in Japan
- Enforcement and Penalties
- Practical Considerations for US Businesses
- Conclusion
In today's interconnected global economy, understanding and complying with local data privacy and cybersecurity regulations is paramount for international businesses. Japan, a major economic powerhouse and a technologically advanced nation, has a sophisticated legal framework governing these areas, primarily centered around the Act on the Protection of Personal Information (APPI) and complemented by cybersecurity initiatives. For US companies operating in or engaging with the Japanese market, navigating these regulations is crucial for building trust, mitigating risks, and ensuring operational continuity.
This article delves into the key aspects of Japan's data protection and cybersecurity landscape, highlighting recent developments and practical considerations for foreign businesses.
I. The Act on the Protection of Personal Information (APPI): Core Principles
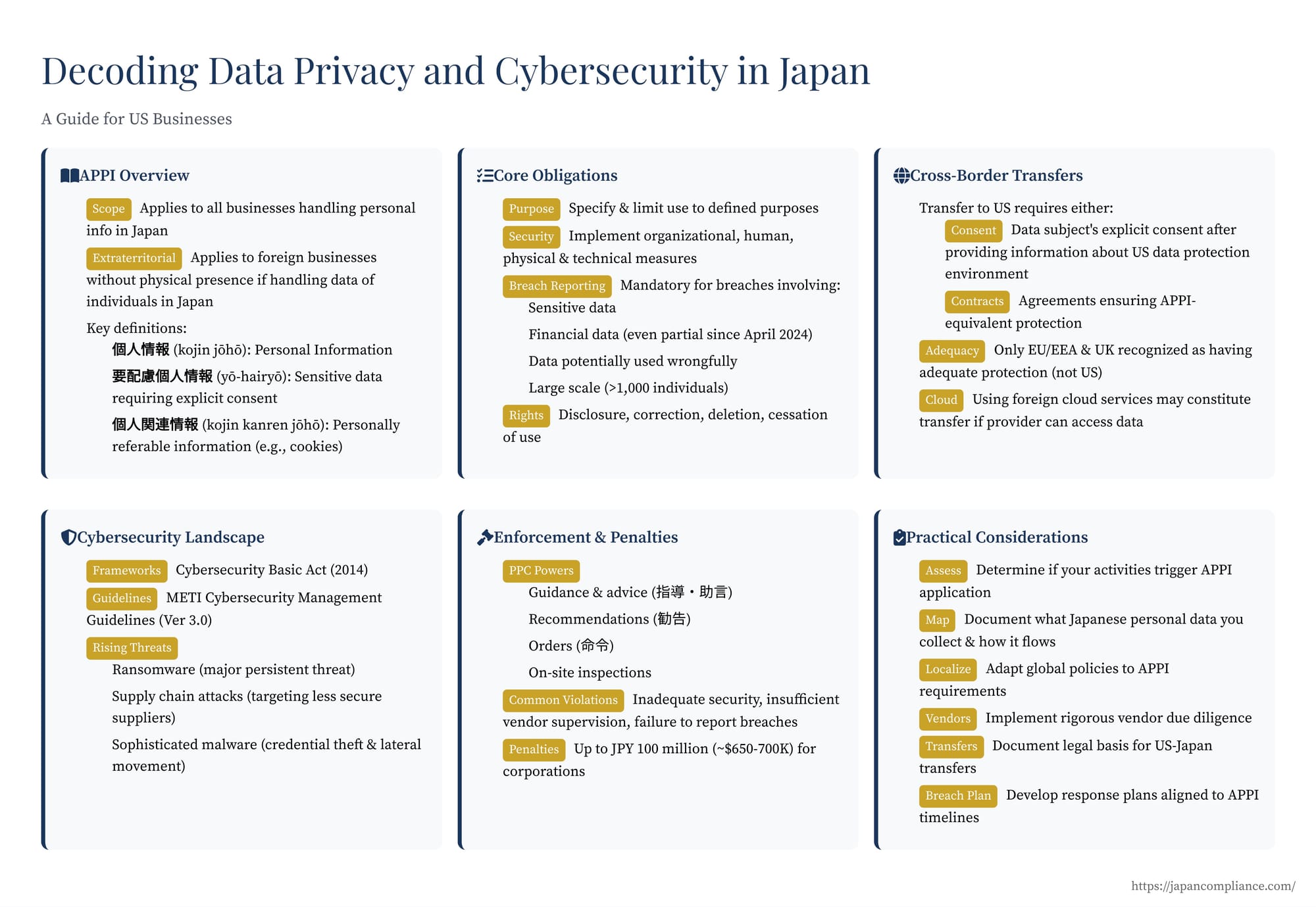
Enacted initially in 2003 and significantly amended several times, most notably with major changes taking full effect in April 2022 and further adjustments in April 2024, the APPI (個人情報保護法 - kojin jōhō hogo hō) establishes the primary rules for handling personal information in Japan. Its enforcement is overseen by the Personal Information Protection Commission (PPC - 個人情報保護委員会, kojin jōhō hogo iinkai), an independent government agency.
A. Scope and Extraterritorial Application
The APPI applies broadly to any "business operator handling personal information" (個人情報取扱事業者 - kojin jōhō toriatsukai jigyōsha), regardless of size or whether they are for-profit or non-profit, when they use such information for their business activities in Japan.
Crucially, the APPI has extraterritorial reach. It applies to foreign businesses, even those without a physical presence in Japan, if they handle the personal information of individuals located in Japan in connection with the provision of goods or services to those individuals. This means many US companies offering online services, e-commerce platforms, or other products directly to Japanese residents fall under the APPI's jurisdiction. Specific guidelines help determine if a foreign business is targeting the Japanese market (e.g., using Japanese language, Japanese currency, .jp domains, or explicitly including Japan in service areas).
B. Key Definitions
Understanding the APPI requires grasping its core definitions:
- Personal Information (個人情報 - kojin jōhō): Information relating to a living individual that can identify the specific individual by name, date of birth, or other description, etc., contained in such information (including information that can be easily collated with other information and thereby identify a specific individual). This is a broad definition.
- Personal Data (個人データ - kojin dēta): Personal information constituting a "personal information database, etc." (systematically organized information). This is the data typically subject to stricter handling requirements like security measures and breach reporting.
- Retained Personal Data (保有個人データ - hoyū kojin dēta): Personal data that a business operator has the authority to disclose, correct, add or delete the contents of, cease the utilization of, erase, and cease the third-party provision of, excluding data prescribed by cabinet order as likely to harm the public or other interests if its presence or absence is known, and data to be erased within a period not exceeding one year. Data subject rights primarily apply to this category.
- Sensitive Personal Information (要配慮個人情報 - yō-hairyō kojin jōhō): Personal information comprising the principal's race, creed, social status, medical history, criminal record, fact of having suffered damage by a crime, or other descriptions, etc., prescribed by cabinet order as those of which the handling requires special consideration so as not to cause unfair discrimination, prejudice or other disadvantage to the principal. Obtaining explicit consent is generally required before acquiring sensitive personal information.
- Pseudonymously Processed Information (仮名加工情報 - kamei kakō jōhō): Introduced by the 2022 amendments, this refers to personal information processed so that the specific individual cannot be identified unless collated with other information. Handling rules are somewhat relaxed (e.g., breach reporting might not be required under certain conditions), aiming to promote data utilization while protecting privacy. Specific processing standards must be met.
- Personally Referable Information (個人関連情報 - kojin kanren jōhō): Also introduced in 2022, this covers information relating to a living individual that does not fall under personal information, pseudonymously processed information, or anonymously processed information (e.g., cookie data, IP addresses, Browse history not easily linkable to an identified individual by the sender). Restrictions apply when this information is transferred to a third party who is expected to link it to personal data. The recipient must generally obtain consent from the data subject prior to receiving such information if they intend to acquire it as personal data.
II. Core Obligations for Businesses Under the APPI
The APPI imposes several key obligations on business operators handling personal information.
A. Purpose Specification and Use Limitation
Businesses must specify the purpose of utilization of personal information as concretely as possible and must not handle personal information beyond the scope necessary to achieve that specified purpose without obtaining prior consent from the individual (the "principal" or 本人 - honnin).
B. Proper Acquisition and Consent
Personal information must be acquired properly, not through deceit or other wrongful means. Sensitive personal information generally cannot be acquired without the principal's prior consent. Consent is also the primary legal basis for many processing activities, including providing personal data to third parties.
C. Data Security Management Measures (安全管理措置 - Anzen Kanri Sochi)
Article 23 of the APPI mandates that business operators take necessary and appropriate measures for the security control of personal data, including preventing leakage, loss, or damage. The PPC guidelines elaborate on these measures, categorizing them into:
- Organizational Security Measures: Establishing internal structures and rules for handling personal data, appointing a responsible person, conducting audits, defining responsibilities.
- Human Security Measures: Training employees, incorporating confidentiality obligations into employment rules.
- Physical Security Measures: Controlling access to physical areas where personal data is handled, securing devices and documents, preventing theft or loss of equipment.
- Technical Security Measures: Implementing access controls (authentication, authorization), protecting against unauthorized access from external networks (firewalls, intrusion detection/prevention), encrypting data where appropriate, logging access, managing vulnerabilities.
The required level of security is based on the nature and volume of the data handled and the potential risks involved. Failure to implement adequate security measures is a common reason for PPC enforcement actions.
D. Supervision of Employees and Contractors (委託先の監督 - Itakusaki no Kantoku)
Businesses must exercise necessary and appropriate supervision over their employees handling personal data. If a business entrusts the handling of personal data to a third party (a contractor or vendor - 委託先, itakusaki), it must exercise necessary and appropriate supervision over that contractor to ensure the security control of the entrusted data. This includes selecting appropriate contractors, contractually obligating them to implement security measures compliant with APPI, and periodically monitoring their performance. This is a critical area, as many data breaches originate from vulnerabilities or negligence at third-party vendors.
E. Restrictions on Third-Party Provision
As a general rule, personal data cannot be provided to a third party without the prior consent of the data subject. Exceptions exist, such as when required by law, necessary for protecting life or property where consent is difficult to obtain, or when data handling is entrusted to a contractor (subject to supervision requirements), or in cases of business succession. The provision of pseudonymously processed information and personally referable information have their own specific rules.
F. Data Breach Reporting and Notification (漏えい等報告・本人通知 - Rōei tō Hōkoku / Honnin Tsūchi)
The amendments effective April 1, 2022, made reporting to the PPC and notification to affected individuals mandatory for certain types of data breaches ("leakage, loss, or damage" - 漏えい等, rōei tō). Mandatory reporting/notification is triggered if the breach involves:
- Sensitive personal information.
- Personal data that may cause property damage if improperly used (e.g., financial account information, credit card numbers without the security code - Note: April 2024 changes expanded this, see below).
- Personal data potentially handled for a wrongful purpose (e.g., breaches caused by unauthorized access, extortion demands).
- A large number of individuals (currently exceeding 1,000).
Businesses must submit a preliminary report to the PPC "promptly" (generally within 3-5 days) after becoming aware of a potential breach falling under these categories, followed by a final report within 30 days (or 60 days for breaches caused by wrongful intent). Notification to affected individuals must also occur promptly.
April 2024 Update: Effective April 1, 2024, the scope of mandatory reporting/notification was subtly expanded. Specifically, under trigger #2 (risk of property damage), the rules were revised to clarify that reporting is required if information that could be used for unauthorized payments (like credit card numbers even without the security code, or online payment service login credentials) is leaked due to actions like web skimming. This change closed a loophole where some businesses previously argued such incidents weren't covered if only partial payment data was compromised by malware injected into their websites. This reflects the PPC's focus on evolving cyber threats.
G. Data Subject Rights (開示等請求権 - Kaiji tō Seikyūken)
Individuals have rights regarding their "retained personal data," including:
- Right to Request Disclosure: Individuals can request disclosure of their retained personal data, including records of third-party transfers. Disclosure must generally be provided digitally if requested.
- Right to Request Correction, Addition, or Deletion: If retained personal data is inaccurate, individuals can request correction, addition, or deletion.
- Right to Request Cessation of Use or Erasure: Individuals can request cessation of use or erasure if their data is handled in violation of purpose limitation rules, acquired improperly, or (under the 2022 changes) if the data is no longer necessary for the business operator, a major breach has occurred, or the handling risks harming the individual's rights or legitimate interests.
- Right to Request Cessation of Third-Party Provision: Individuals can request cessation of provision to third parties if done without consent or (under the 2022 changes) if the provision risks harming the individual's rights or legitimate interests.
Businesses must establish procedures to handle these requests appropriately and respond without delay.
III. Cross-Border Data Transfers
Transferring personal data outside of Japan is subject to specific rules under Article 28 of the APPI. The default requirement is obtaining the principal's prior consent for the transfer to a third party located in a foreign country.
However, there are alternatives to consent:
- Transfer to Countries with Equivalent Protection (Adequacy Decision): Transfers are permitted without specific consent if the recipient country is designated by the PPC as having a data protection system recognized as equivalent to Japan's. Currently, only the European Economic Area (EEA) countries and the United Kingdom hold this status. The US does not have an adequacy decision from Japan.
- Recipient Has Equivalent System: Transfers are permitted if the foreign recipient has established a system to continuously take measures equivalent to those required of Japanese business operators under the APPI. This typically involves:
- Contractual Agreements: Entering into a contract between the data exporter and importer that ensures the importer implements APPI-equivalent measures.
- Intra-Group Rules: Utilizing binding corporate rules within a group of companies that guarantee APPI-equivalent protection, provided these rules are appropriately implemented and enforced.
- Certifications: Relying on recognized frameworks or certifications, although specific cross-border certification schemes are still developing.
When relying on consent or the "equivalent system" mechanism, the transferring business operator has information provision obligations towards the data subject. Upon request (or sometimes proactively when obtaining consent), they must provide information regarding the recipient's data protection environment, such as the name of the foreign country, an overview of its data protection laws, and the measures the recipient takes to protect personal information. This requirement, strengthened in 2022, aims to enhance transparency for data subjects.
Implications for Transfers to the US: Since the US lacks an adequacy decision, transfers of personal data from Japan to the US generally require either:
- The data subject's explicit consent, obtained after providing necessary information about the US data protection environment (which can be complex).
- Implementing contractual clauses or binding corporate rules ensuring the US recipient adheres to APPI-equivalent standards, coupled with an assessment confirming such adherence is practically possible given US laws and practices (potentially considering surveillance laws, similar to Schrems II considerations in the EU context) and fulfilling information provision duties.
Cloud Services: Using cloud services provided by foreign operators where servers are located abroad can constitute a cross-border transfer if the cloud provider can "access" the data. If the provider merely stores encrypted data and cannot access the content, it might not be considered a "provision" to a third party, but the assessment is fact-specific. Regardless, the Japanese business using the cloud service remains responsible for ensuring the data's security, including supervising the cloud provider as a contractor.
IV. The Cybersecurity Landscape in Japan
While the APPI mandates security measures for personal data, Japan's broader cybersecurity posture involves other laws and initiatives.
A. Key Legislation and Guidelines
- Cybersecurity Basic Act (サイバーセキュリティ基本法 - Cyber Security Kihon Hō): Enacted in 2014, this act establishes the foundational framework for cybersecurity policy in Japan. It created the National center of Incident readiness and Strategy for Cybersecurity (NISC) within the Cabinet Secretariat, responsible for coordinating government cybersecurity efforts and developing strategy.
- Critical Infrastructure Protection: Various sector-specific laws and guidelines address cybersecurity for critical infrastructure (finance, energy, transportation, healthcare, etc.). NISC also provides overarching guidance.
- METI's Cybersecurity Management Guidelines (サイバーセキュリティ経営ガイドライン): Issued by the Ministry of Economy, Trade and Industry (METI), these widely referenced guidelines (currently Ver 3.0) provide practical recommendations for corporate management to take leadership in cybersecurity. They emphasize recognizing cybersecurity as a key management issue, building defense systems, and ensuring effective responses, including supply chain risk management.
- MIC Guidelines: The Ministry of Internal Affairs and Communications (MIC) issues guidelines related to telecommunications security and IoT device security.
B. Rising Threats and Regulatory Responses
Japan faces the same escalating cyber threats seen globally. NISC annual reports consistently highlight:
- Ransomware: A major and persistent threat, impacting businesses of all sizes and critical infrastructure (e.g., a significant port disruption in 2023). Attacks often exploit vulnerabilities in VPNs or remote desktop services. Double extortion (encrypting data and threatening to leak stolen data) is common.
- Supply Chain Attacks: Increasing recognition that attacks often target less secure suppliers or subsidiaries to gain access to larger corporate networks. Managing third-party risk is crucial.
- Sophisticated Malware: Threats like Emotet continue to evolve, employing various techniques to steal credentials and spread laterally.
While Japan currently relies heavily on guidelines and voluntary measures for general corporate cybersecurity (outside specific critical sectors), there is growing awareness of stricter regulatory approaches internationally, such as the EU's NIS2 Directive and Cyber Resilience Act. Discussions occur within Japan about potentially strengthening mandatory requirements, particularly concerning incident reporting and security standards for connected devices (e.g., through the JC-STAR IoT security labeling scheme), to enhance overall cyber resilience.
V. Enforcement and Penalties
The PPC actively oversees compliance with the APPI. Its enforcement toolkit includes:
- Guidance and Advice (指導・助言 - Shidō / Jogen): Providing recommendations for improvement.
- Recommendations (勧告 - Kankoku): Issuing formal recommendations to cease violations and take corrective actions. Non-compliance can lead to orders.
- Orders (命令 - Meirei): Ordering corrective actions. Failure to comply with an order can result in imprisonment or hefty fines.
- On-site Inspections and Reporting Requests: The PPC has the power to request reports and conduct inspections, including potentially at foreign entities under its extraterritorial reach (often in cooperation with foreign authorities).
Common Enforcement Themes: Based on publicly available information about PPC actions (often anonymized summaries):
- Inadequate Security Measures: Failure to implement sufficient technical or organizational safeguards leading to breaches (e.g., improper access controls, unpatched vulnerabilities, misconfigured servers).
- Insufficient Vendor Supervision: Breaches occurring due to negligence or misconduct at third-party contractors, where the primary business operator failed in its supervisory duties. Incidents involving unauthorized data access by temporary or dispatched employees at vendors have drawn attention.
- Failure to Report/Notify: Not reporting mandatory breaches to the PPC or notifying affected individuals within the required timeframes.
- Improper Handling: Violations related to consent, purpose limitation, or handling of sensitive data. Issues with opt-out mechanisms for data sharing have also been subject to scrutiny.
Increased Penalties: The 2022 APPI amendments significantly increased potential penalties. Fines for corporations failing to comply with PPC orders or providing false reports can now reach up to JPY 100 million (approx. USD 650,000-700,000 depending on exchange rates). Individuals responsible can also face criminal penalties.
VI. Practical Considerations for US Businesses
Navigating Japan's data protection and cybersecurity requires a proactive and localized approach:
- Determine Applicability: Assess whether your business activities trigger the APPI's extraterritorial scope.
- Data Mapping: Understand what personal information of individuals in Japan you collect, how it is used, stored, and transferred (including cross-border).
- Appoint a Representative: Foreign businesses subject to APPI may need to designate a representative in Japan under certain circumstances, although the specific requirements are nuanced.
- Review and Localize Policies: Ensure your global privacy policy and internal procedures align with APPI requirements. Translate relevant documents into Japanese where necessary for clarity and compliance (e.g., privacy notices for Japanese data subjects).
- Implement Robust Security: Align security measures with APPI requirements and recognized best practices (like METI guidelines), considering both technical and organizational aspects.
- Vendor Due Diligence: Implement rigorous processes for vetting and supervising vendors handling personal data from Japan. Ensure contracts include appropriate data protection clauses.
- Cross-Border Transfer Strategy: Carefully evaluate and document the legal basis for any transfers of personal data from Japan to the US or other countries (consent, contracts, etc.), fulfilling associated information provision duties.
- Breach Response Plan: Develop and test an incident response plan tailored to APPI's reporting and notification timelines and requirements.
- Employee Training: Train employees, both in the US and Japan (if applicable), on APPI requirements and secure data handling practices.
Conclusion
Japan's legal framework for data privacy and cybersecurity is robust and evolving. The APPI, particularly after its recent amendments, imposes significant obligations on businesses handling personal information of individuals in Japan, including those operating from overseas. Coupled with a challenging cybersecurity threat landscape, compliance requires ongoing diligence, investment in security measures, and a clear understanding of specific requirements like cross-border transfer rules and breach reporting mandates. For US businesses seeking to thrive in the Japanese market, integrating APPI compliance and strong cybersecurity practices into their operational DNA is not just a legal necessity but a strategic imperative for building trust and ensuring long-term success.
- Personal Information Protection Commission – APPI Guidelines & FAQs
- NISC Cybersecurity Strategy & Incident Reports
- METI Cybersecurity Management Guidelines (English Digest)
