Data Security in Japanese Litigation: What the Digital Shift Means for Your Business
TL;DR
Japan’s court-digitalization program (e-filing, remote hearings, e-case files) offers speed and convenience—but also concentrates sensitive data in new online systems. Businesses must harden endpoint security, use MFA, control evidence handling, and follow court protocols to avoid breaches or evidence tampering.
Table of Contents
- The New Digital Landscape and Its Security Implications
- Key Security Risks in Digitalized Litigation
- Safeguards in Japan’s Digital Litigation Framework
- User Responsibilities: The Shared Security Burden
- Electronic Evidence: Integrity and Authentication
- Conclusion: Embracing Digital Justice Securely
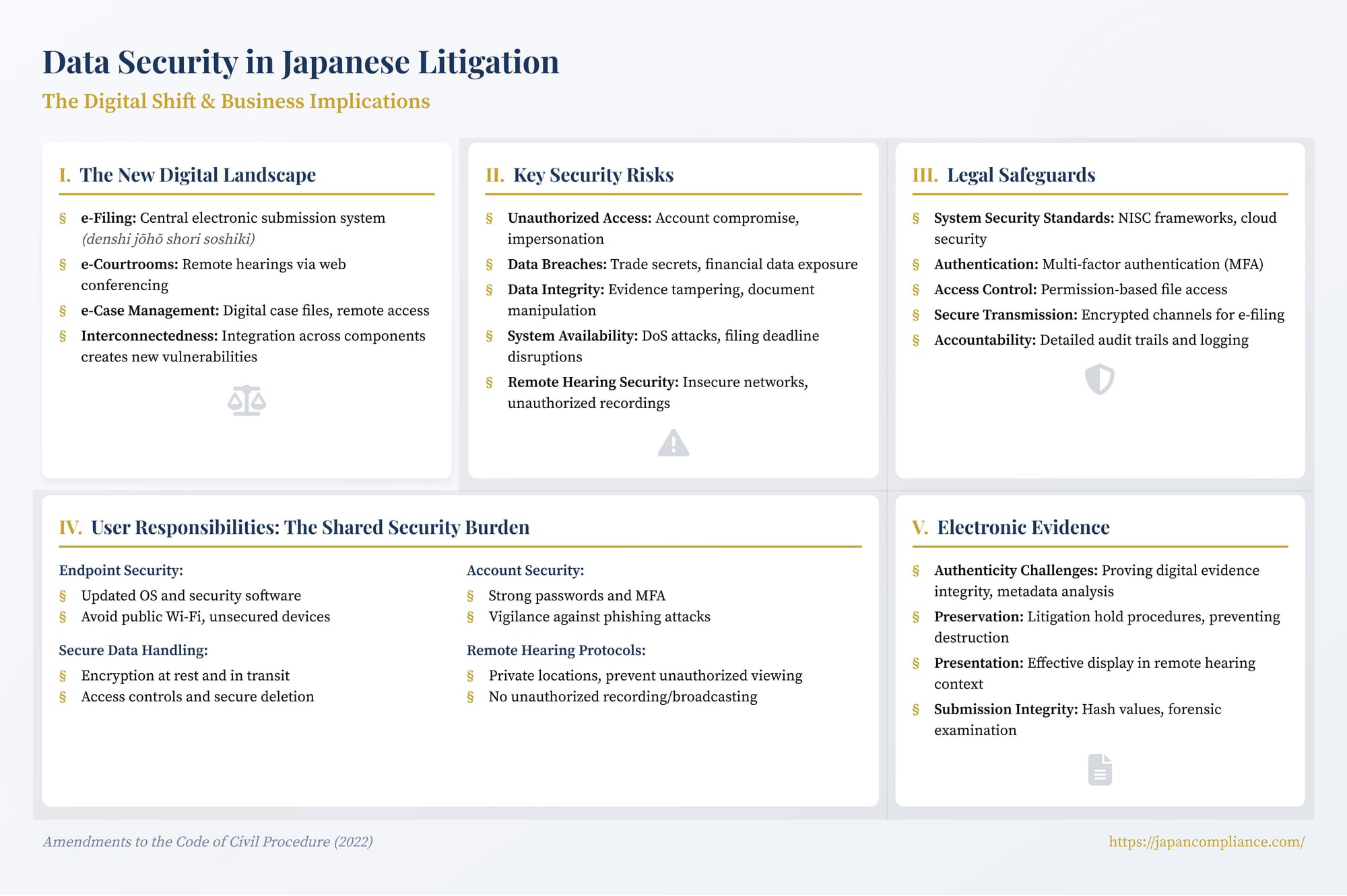
As Japan implements its ambitious plan to digitalize civil court procedures, the landscape of litigation is set to change dramatically. The move towards e-filing, remote hearings via web conferencing, and electronic case management promises greater efficiency and accessibility. However, this digital transformation, mandated by the 2022 amendments to the Code of Civil Procedure, also brings data security to the forefront. For international businesses involved in Japanese litigation, protecting sensitive information – from proprietary trade secrets submitted as evidence to the personal data of employees – within this new digital ecosystem is a critical concern.
The transition from a predominantly paper-based system to one reliant on electronic data transmission and storage introduces new vulnerabilities and necessitates a heightened focus on cybersecurity from all participants: the courts, legal representatives, and the parties themselves. Understanding the potential risks, the safeguards being implemented, and the responsibilities of users is crucial for navigating this new era securely. This article explores the key data security considerations arising from Japan's civil procedure digitalization and what they mean for businesses operating within the Japanese legal system.
The New Digital Landscape and Its Security Implications
The core components of the reform – e-filing, e-courtrooms, and e-case management – fundamentally alter how litigation data is created, transmitted, stored, and accessed, each presenting unique security considerations:
- e-Filing & e-Case Management: Submitting documents electronically through a central court system (denshi jōhō shori soshiki – electronic information processing system) and maintaining the entire case file digitally means vast amounts of potentially sensitive information reside on court-managed servers. This central repository becomes a target, requiring robust protection against unauthorized access, data breaches, ransomware, and tampering. Furthermore, the planned ability for parties to access these electronic records remotely increases the attack surface and necessitates secure authentication and access controls.
- e-Courtroom (Remote Hearings): Conducting preparatory proceedings and even formal oral arguments via web conferencing introduces risks associated with the communication channel and the participants' environments. These include potential eavesdropping on confidential discussions, unauthorized recording of proceedings, the possibility of impersonation (if identity verification is weak), and disruptions due to unstable connections or denial-of-service attacks targeting the platform.
- Interconnectedness: The integration of these components means a security failure in one part (e.g., compromised user credentials for e-filing) could potentially expose other parts of the system or case data.
Key Security Risks in Digitalized Litigation
Businesses involved in Japanese digital litigation should be aware of several key risk categories:
- Unauthorized Access and Impersonation: Compromised user accounts (belonging to lawyers, parties, or even court staff) could allow malicious actors to access confidential case files, submit fraudulent documents, or disrupt proceedings. Weak identity verification at the registration stage or inadequate login authentication (e.g., lack of robust multi-factor authentication - MFA) increases this risk. Impersonating a party or lawyer during a remote hearing is also a theoretical possibility.
- Data Breaches and Confidentiality Violations: The concentration of sensitive case information in digital format elevates the risk of large-scale data breaches through hacking or insider threats. Accidental disclosure through misdirected electronic communications or insecure handling of downloaded case files by users is also a concern. This includes not only case strategy documents but also evidence containing trade secrets, financial data, personal information of employees or customers, etc.
- Data Integrity and Tampering: Ensuring that electronic court records and submitted evidence have not been altered is crucial for the integrity of the judicial process. Digital files can be easier to manipulate undetectably than paper documents if proper safeguards (like cryptographic hashing, secure logging, access controls) are not rigorously implemented and maintained. Tampering could occur either within the court system or before evidence is submitted.
- System Availability and Denial of Service: Reliance on a central IT system makes court operations vulnerable to technical failures or denial-of-service (DoS) attacks. System downtime could impede filing deadlines, delay hearings, and disrupt the overall administration of justice.
- Remote Hearing Security: Conducting hearings remotely requires secure communication channels and protocols. Using unsecured networks (like public Wi-Fi) for participation significantly increases the risk of interception. Preventing participants or others present at their location from making unauthorized recordings or broadcasts is also a challenge.
Safeguards in Japan's Digital Litigation Framework
Recognizing these risks, the Japanese government and judiciary are incorporating security considerations into the design and implementation of the digital system. While specific technical details are often determined by Supreme Court rules and system specifications (many still under development for the full Phase 3 implementation), the legislative framework and related discussions point to several intended safeguards:
- System Security Standards: The court's central electronic information processing system is expected to adhere to high security standards, likely drawing from government-wide cybersecurity frameworks (such as those from the National center of Incident readiness and Strategy for Cybersecurity - NISC). Parliamentary deliberations during the law's passage emphasized the need for robust measures against cyberattacks and data leakage. The use of cloud services, aligned with the government's "Cloud by Default" policy, necessitates careful selection of providers and implementation of appropriate security controls, including considerations for data residency.
- Authentication and Access Control: Secure access is fundamental. While details will emerge in Supreme Court rules, it's anticipated that legal professionals will require strong authentication, likely involving multi-factor authentication (MFA), to access the e-filing and case management systems. Identity verification procedures will be necessary during user registration, although ensuring their rigor, especially for self-represented parties, remains a practical challenge. Access to specific case files will be permission-based, limiting visibility to authorized parties, their representatives, and court personnel.
- Secure Transmission and Filing: E-filing is intended to occur over secure channels. The system itself will likely incorporate measures to validate file integrity upon upload. The development of the "mints" system provides an early example, requiring users to register and log in to a dedicated portal.
- Accountability and Logging: Digital systems allow for detailed logging of user actions (logins, file access, submissions, etc.). These audit trails are crucial for accountability, investigating security incidents, and potentially verifying procedural steps (e.g., confirming when a document was electronically served or accessed). This addresses risks of non-repudiation (users denying actions they took).
- Data Minimization & Concealment: The new provisions allowing parties to request concealment of their name, address, and other identifying information (Articles 133ff of the amended Code) serve a dual purpose. Primarily for victim protection, they also function as a data minimization tool within the digital record, limiting the exposure of sensitive personal data to opposing parties and third-party viewers where justified.
- Physical Media Security (Where Applicable): While the goal is digitalization, the law still acknowledges situations where physical media (like USB drives) might be used for submitting or exchanging copies of electronic records (e.g., Article 132-6). The law mandates appropriate security measures for managing electronically stored information held by the court (Article 92-9), and best practices strongly recommend encryption, password protection, and secure deletion for any necessary physical transfer or storage of litigation data on portable media.
User Responsibilities: The Shared Security Burden
While the court system provides the infrastructure, ensuring data security in digital litigation is a shared responsibility. Lawyers, parties, and their supporting staff play a critical role:
- Endpoint Security: Devices used to access the court system (PCs, laptops, tablets) must be secured. This includes:
- Using up-to-date operating systems and security software (antivirus, anti-malware).
- Implementing firewalls.
- Avoiding the use of personal or shared devices for accessing sensitive case information.
- Refraining from using unsecured networks, especially public Wi-Fi, for court-related activities.
- Account Security: User credentials are prime targets. Best practices include:
- Using strong, unique passwords.
- Enabling and securely managing MFA methods.
- Being vigilant against phishing attacks designed to steal login details.
- Immediately reporting any suspected account compromise to both the firm/company IT department and potentially the court authorities.
- Secure Data Handling: Digitized case files require careful management:
- Implementing access controls on local or network drives where case files are stored.
- Encrypting sensitive documents, both at rest and in transit (e.g., when emailing drafts internally, though sensitive communications should ideally use secure platforms).
- Securely deleting or disposing of digital case files when no longer needed, according to retention policies and ethical obligations.
- Remote Hearing Protocols:
- Participating from a private, secure location where conversations cannot be overheard.
- Ensuring no unauthorized individuals are present or able to view the screen.
- Strictly adhering to court rules prohibiting unauthorized recording or broadcasting.
- Training and Awareness: Regular cybersecurity awareness training for legal teams and relevant business personnel involved in litigation is crucial. This should cover phishing prevention, password security, secure data handling, and awareness of social engineering tactics.
Electronic Evidence: Integrity and Authentication
The move to digital procedures also impacts how electronic evidence is handled and perceived:
- Authenticity Challenges: Proving the authenticity and integrity of digital evidence (emails, chat logs, databases, electronically signed documents) can be more complex than with paper documents. Metadata analysis, digital forensics, and understanding the source system's reliability become more important. The court's e-filing system might provide some integrity checks upon submission (e.g., hash values), but it cannot guarantee the authenticity of a document before it was submitted. Alterations made prior to filing remain a challenge detectable primarily through forensic examination or inconsistencies with other evidence.
- Preservation: Parties have an obligation to preserve potentially relevant electronic evidence once litigation is anticipated. The ease with which digital data can be deleted or modified underscores the importance of implementing robust litigation hold procedures internally.
- Presentation: Effectively presenting complex digital evidence in a remote hearing format might require new techniques and technologies beyond simple screen sharing.
While Japan does not have the broad, formalized e-discovery processes common in the US, the principles of preserving, authenticating, and securely presenting digital evidence are increasingly relevant in the digitalized court environment.
Conclusion: Embracing Digital Justice Securely
The digitalization of Japan's civil litigation system marks a significant step towards modernization and efficiency. However, it inherently introduces new data security challenges that demand attention from the courts, legal practitioners, and the businesses involved in disputes. Robust security for the court's IT infrastructure, coupled with diligent cybersecurity practices by all users, is essential to maintain the confidentiality, integrity, and availability of sensitive litigation data.
For international companies, this means not only adapting to new digital workflows for filing documents and attending hearings but also embedding strong data security protocols into their litigation management processes. This includes securing endpoints, managing user credentials carefully, handling digital case files responsibly, ensuring secure participation in remote hearings, and being mindful of the nuances of electronic evidence. By understanding the risks and adopting proactive security measures, businesses can confidently engage with Japan's evolving digital justice system while protecting their valuable information.
